【2023最新】超详细!!!新商盟卷烟js逆向_包括验证码错误问题
前言
新商盟卷烟 密码 js 逆向
密码加密好解决,但是多次请求,还会有一个验证码
这个时候就会请求失败
所以验证码问题我也会解决
1 抓包
先模拟登录,抓到返回表单的包
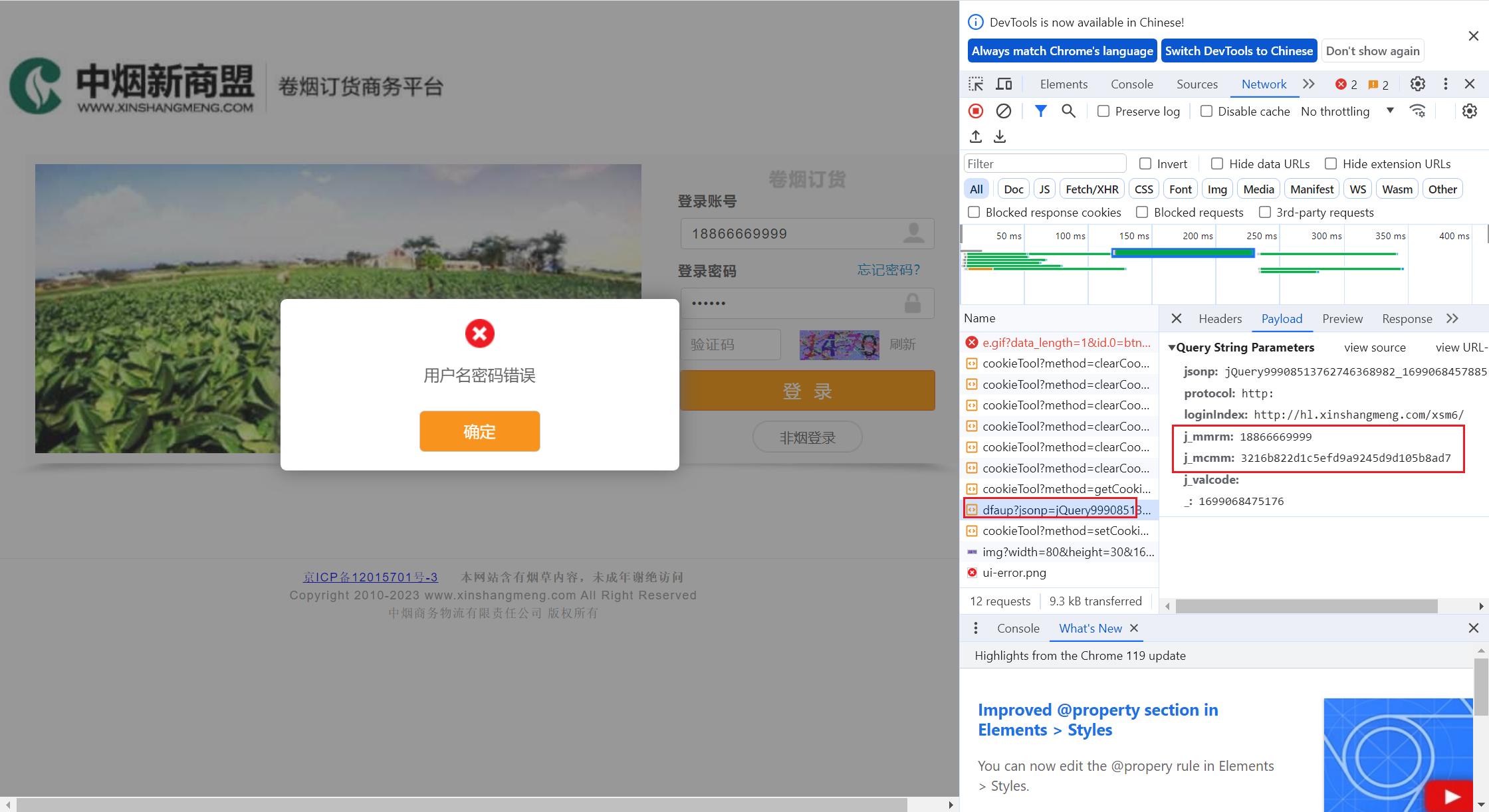
2 搜素加密字段
输入加密的字段,搜索js文件打断点调试
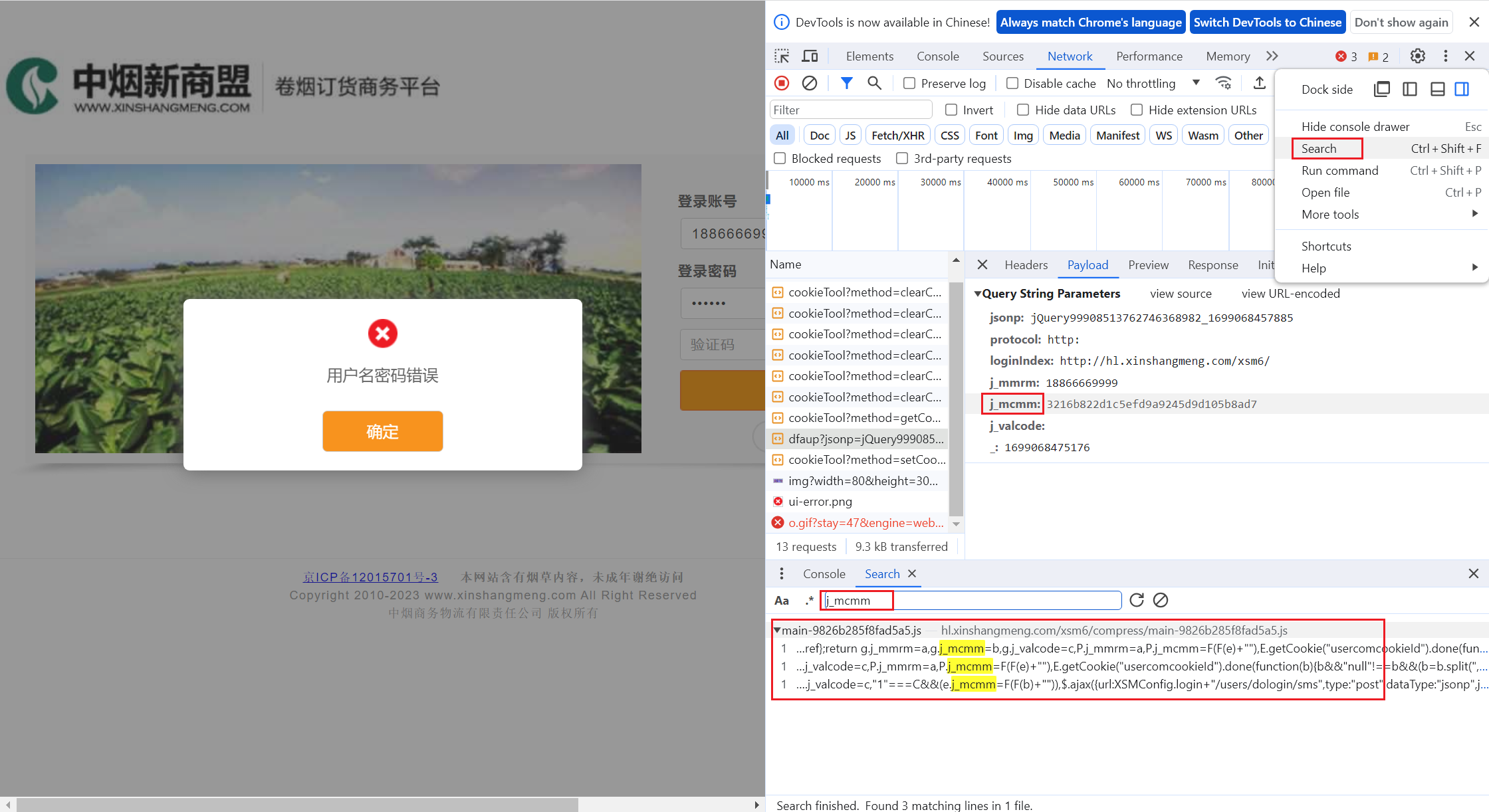
3 断点调试
在可疑的字段处打上断点
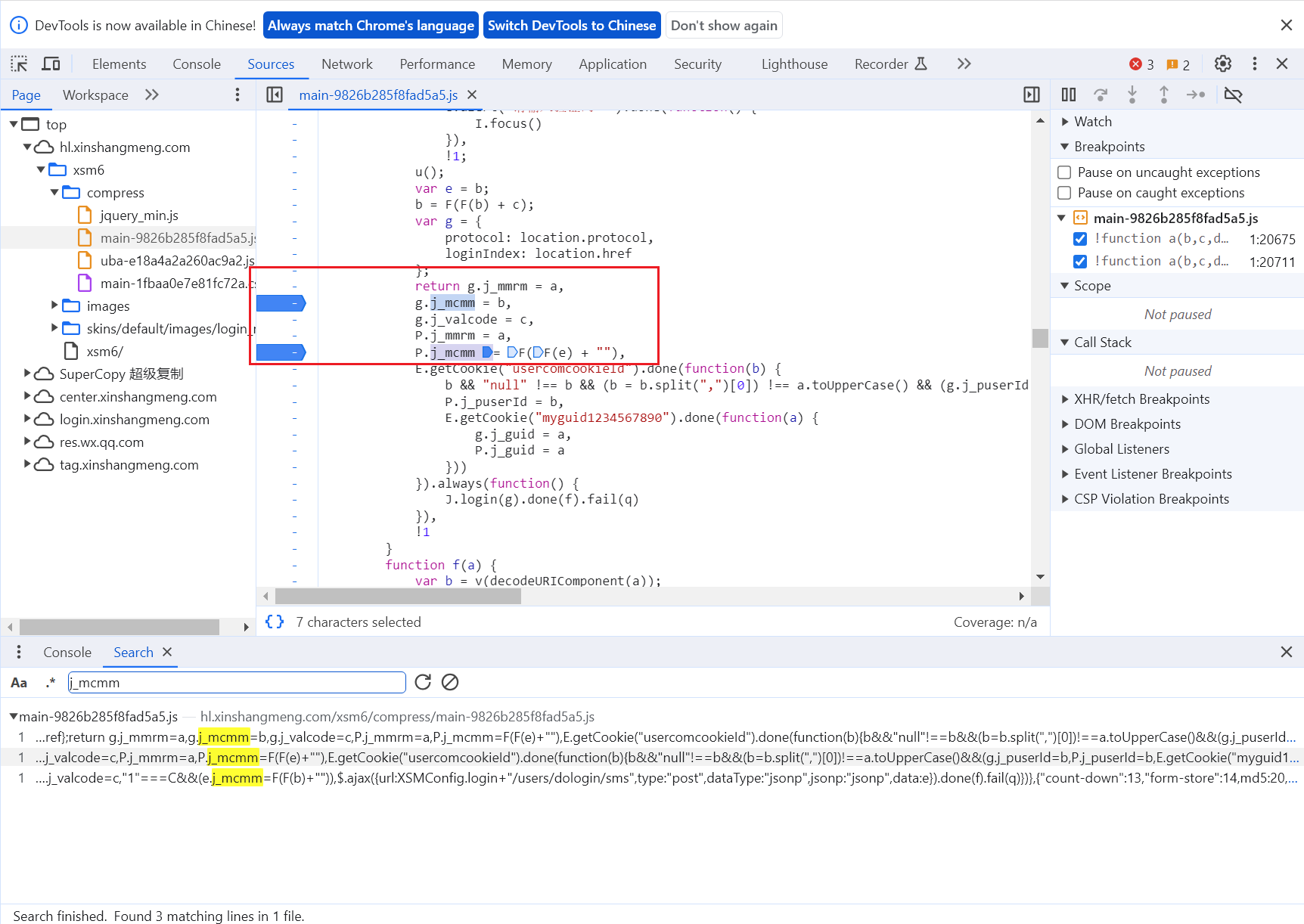
再次输入进行调试
调试后我们发现有两个字段不能确定哪一个是加密字段,但是我们现在可以看到
c是验证码
g.j_mcmm是有验证码的返回值
p.j_mcmm是没有验证码的返回值,我们这里退出调试,看看最后的返回值是哪一个
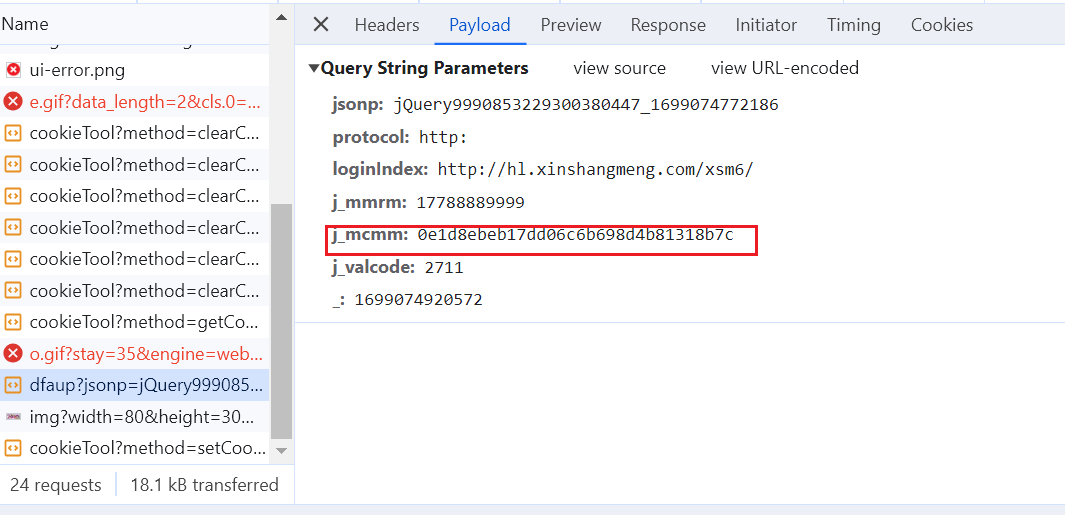
退出之后可以看到返回的是g.j_mcmm,说明他是加了验证码的
所以:F(F(b)+c) 就是我们需要的函数
b是你的密码
c是验证码
先把b用F函数加密一次
在把加密后的密码加上验证码在加密一次
就是返回的值
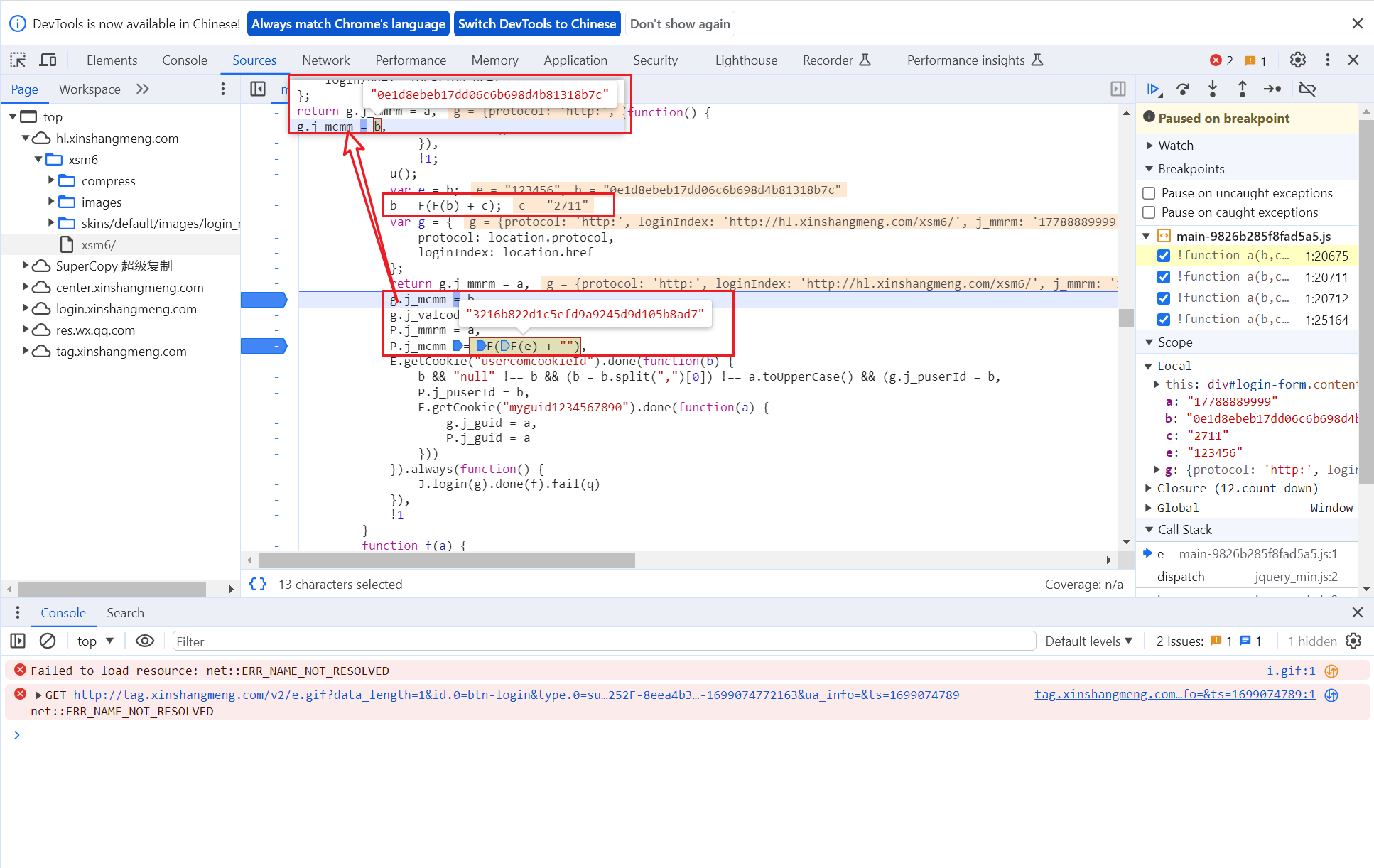
4 js扣代码还原
找到F函数,打上断点查看
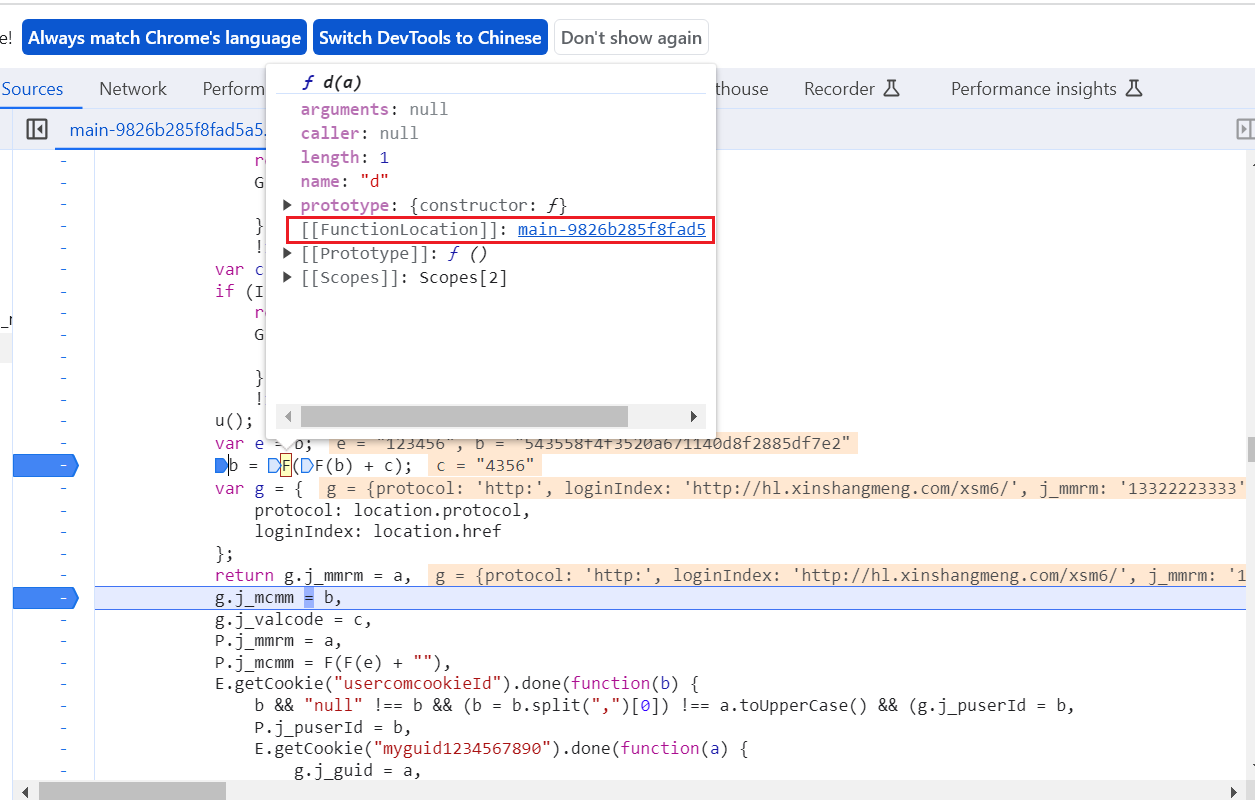
找到之后打上断点调试
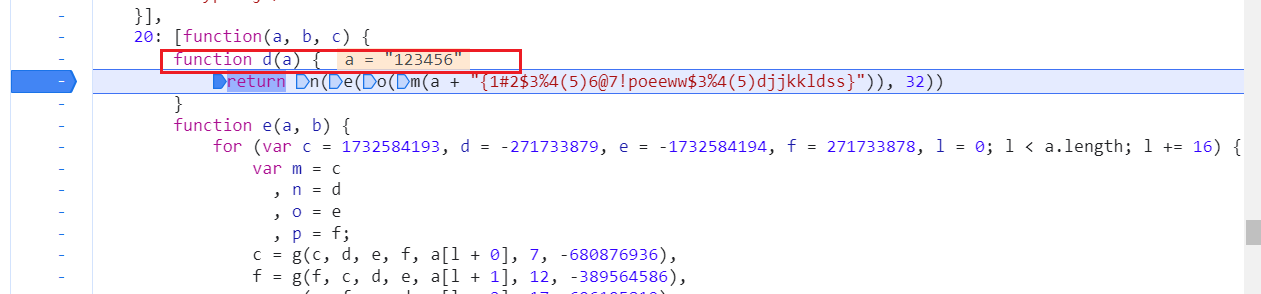
可以看到d就是F函数,参数a就是密码
经过了n,e,o,m函数多次加密就是返回值
所以我们直接扣js代码,记得把n,e,o,m函数也带上
// js代码
function e(a, b) {
for (var c = 1732584193, d = -271733879, e = -1732584194, f = 271733878, l = 0; l < a.length; l += 16) {
var m = c
, n = d
, o = e
, p = f;
c = g(c, d, e, f, a[l + 0], 7, -680876936),
f = g(f, c, d, e, a[l + 1], 12, -389564586),
e = g(e, f, c, d, a[l + 2], 17, 606105819),
d = g(d, e, f, c, a[l + 3], 22, -1044525330),
c = g(c, d, e, f, a[l + 4], 7, -176418897),
f = g(f, c, d, e, a[l + 5], 12, 1200080426),
e = g(e, f, c, d, a[l + 6], 17, -1473231341),
d = g(d, e, f, c, a[l + 7], 22, -45705983),
c = g(c, d, e, f, a[l + 8], 7, 1770035416),
f = g(f, c, d, e, a[l + 9], 12, -1958414417),
e = g(e, f, c, d, a[l + 10], 17, -42063),
d = g(d, e, f, c, a[l + 11], 22, -1990404162),
c = g(c, d, e, f, a[l + 12], 7, 1804603682),
f = g(f, c, d, e, a[l + 13], 12, -40341101),
e = g(e, f, c, d, a[l + 14], 17, -1502002290),
d = g(d, e, f, c, a[l + 15], 22, 1236535329),
c = h(c, d, e, f, a[l + 1], 5, -165796510),
f = h(f, c, d, e, a[l + 6], 9, -1069501632),
e = h(e, f, c, d, a[l + 11], 14, 643717713),
d = h(d, e, f, c, a[l + 0], 20, -373897302),
c = h(c, d, e, f, a[l + 5], 5, -701558691),
f = h(f, c, d, e, a[l + 10], 9, 38016083),
e = h(e, f, c, d, a[l + 15], 14, -660478335),
d = h(d, e, f, c, a[l + 4], 20, -405537848),
c = h(c, d, e, f, a[l + 9], 5, 568446438),
f = h(f, c, d, e, a[l + 14], 9, -1019803690),
e = h(e, f, c, d, a[l + 3], 14, -187363961),
d = h(d, e, f, c, a[l + 8], 20, 1163531501),
c = h(c, d, e, f, a[l + 13], 5, -1444681467),
f = h(f, c, d, e, a[l + 2], 9, -51403784),
e = h(e, f, c, d, a[l + 7], 14, 1735328473),
d = h(d, e, f, c, a[l + 12], 20, -1926607734),
c = i(c, d, e, f, a[l + 5], 4, -378558),
f = i(f, c, d, e, a[l + 8], 11, -2022574463),
e = i(e, f, c, d, a[l + 11], 16, 1839030562),
d = i(d, e, f, c, a[l + 14], 23, -35309556),
c = i(c, d, e, f, a[l + 1], 4, -1530992060),
f = i(f, c, d, e, a[l + 4], 11, 1272893353),
e = i(e, f, c, d, a[l + 7], 16, -155497632),
d = i(d, e, f, c, a[l + 10], 23, -1094730640),
c = i(c, d, e, f, a[l + 13], 4, 681279174),
f = i(f, c, d, e, a[l + 0], 11, -358537222),
e = i(e, f, c, d, a[l + 3], 16, -722521979),
d = i(d, e, f, c, a[l + 6], 23, 76029189),
c = i(c, d, e, f, a[l + 9], 4, -640364487),
f = i(f, c, d, e, a[l + 12], 11, -421815835),
e = i(e, f, c, d, a[l + 15], 16, 530742520),
d = i(d, e, f, c, a[l + 2], 23, -995338651),
c = j(c, d, e, f, a[l + 0], 6, -198630844),
f = j(f, c, d, e, a[l + 7], 10, 1126891415),
e = j(e, f, c, d, a[l + 14], 15, -1416354905),
d = j(d, e, f, c, a[l + 5], 21, -57434055),
c = j(c, d, e, f, a[l + 12], 6, 1700485571),
f = j(f, c, d, e, a[l + 3], 10, -1894986606),
e = j(e, f, c, d, a[l + 10], 15, -1051523),
d = j(d, e, f, c, a[l + 1], 21, -2054922799),
c = j(c, d, e, f, a[l + 8], 6, 1873313359),
f = j(f, c, d, e, a[l + 15], 10, -30611744),
e = j(e, f, c, d, a[l + 6], 15, -1560198380),
d = j(d, e, f, c, a[l + 13], 21, 1309151649),
c = j(c, d, e, f, a[l + 4], 6, -145523070),
f = j(f, c, d, e, a[l + 11], 10, -1120210379),
e = j(e, f, c, d, a[l + 2], 15, 718787259),
d = j(d, e, f, c, a[l + 9], 21, -343485551),
c = k(c, m),
d = k(d, n),
e = k(e, o),
f = k(f, p)
}
return new Array(c,d,e,f)
}
function f(a, b, c, d, e, f) {
return k(l(k(k(b, a), k(d, f)), e), c)
}
function g(a, b, c, d, e, g, h) {
return f(b & c | ~b & d, a, b, e, g, h)
}
function h(a, b, c, d, e, g, h) {
return f(b & d | c & ~d, a, b, e, g, h)
}
function i(a, b, c, d, e, g, h) {
return f(b ^ c ^ d, a, b, e, g, h)
}
function j(a, b, c, d, e, g, h) {
return f(c ^ (b | ~d), a, b, e, g, h)
}
function k(a, b) {
var c = (65535 & a) + (65535 & b);
return (a >> 16) + (b >> 16) + (c >> 16) << 16 | 65535 & c
}
function l(a, b) {
return a << b | a >>> 32 - b
}
function m(a) {
for (var b = a.length, c = new Array(b), d = 0; d < b; d++) {
var e = a.charCodeAt(d);
c[d] = 255 & e
}
return c
}
function n(a) {
for (var b = "0123456789abcdef", c = "", d = 0; d < 4 * a.length; d++)
c += b.charAt(a[d >> 2] >> d % 4 * 8 + 4 & 15) + b.charAt(a[d >> 2] >> d % 4 * 8 & 15);
return c
}
function o(a) {
for (var b = 1 + (a.length + 8 >> 6), c = new Array(16 * b), d = 0; d < 16 * b; d++)
c[d] = 0;
for (var e = 0; e < a.length; e++)
c[e >> 2] |= (255 & a[e]) << e % 4 * 8;
return c[e >> 2] |= 128 << e % 4 * 8,
c[16 * b - 2] = 8 * a.length,
c
}
function d(a) {
return n(e(o(m(a + "{1#2$3%4(5)6@7!poeeww$3%4(5)djjkkldss}")), 32))
}
// var c = '4356'
var c = ''
function pwd(a) {
return d(d(a) + c)
}
// console.log(pwd(123456))
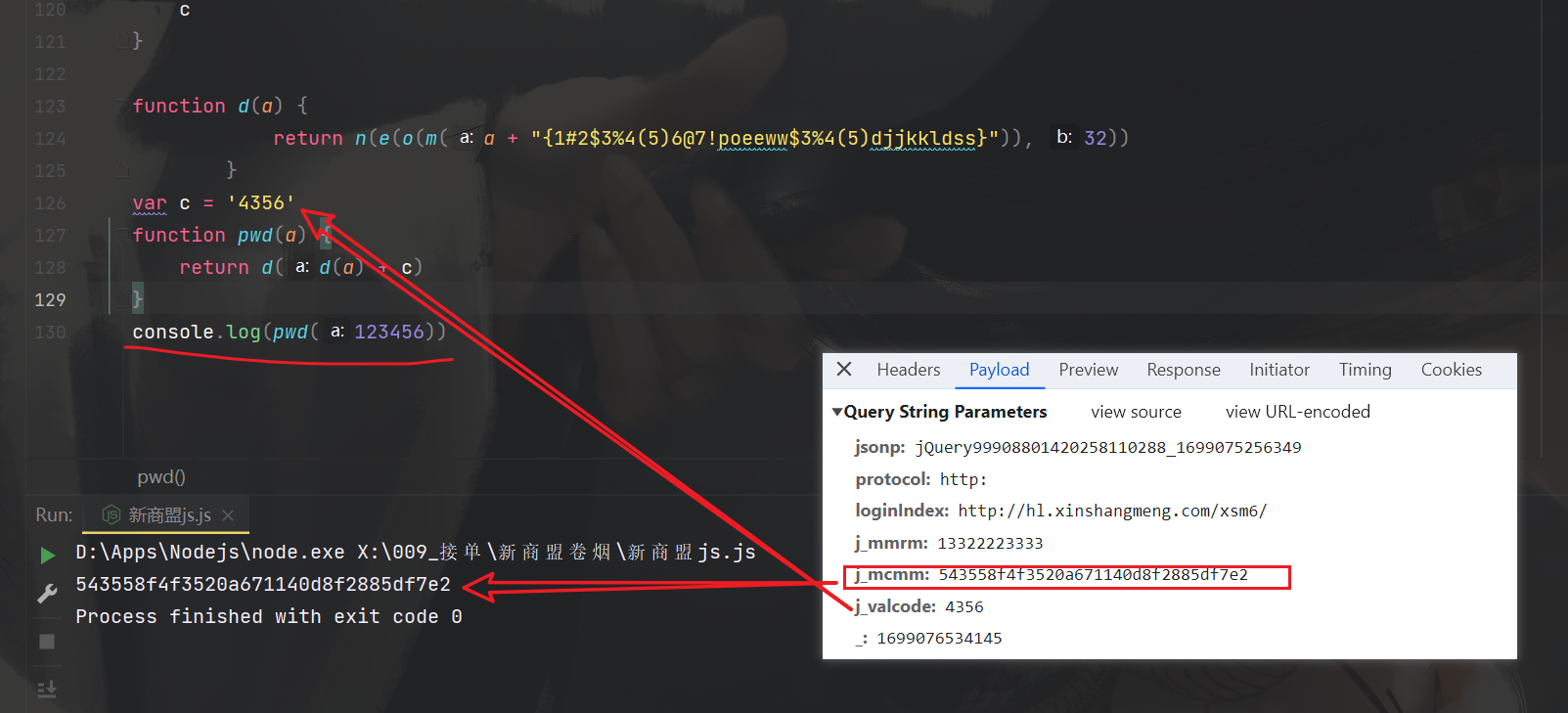
可以看到这里也是非常的成功
但是这个验证码是个活动的值,他不唯一
所以我们想要真正的登录成功,需要破解验证码
5 破解验证码
我们第一次的时候就没有验证码,为什么后面就有了呢?
因为cookies,下面的cookies是有验证码的cookie
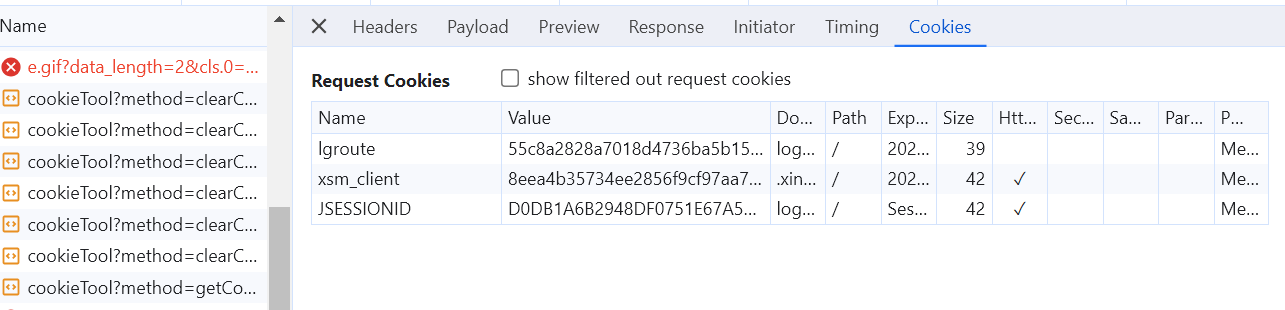
我们把cookies全部删除在试一次
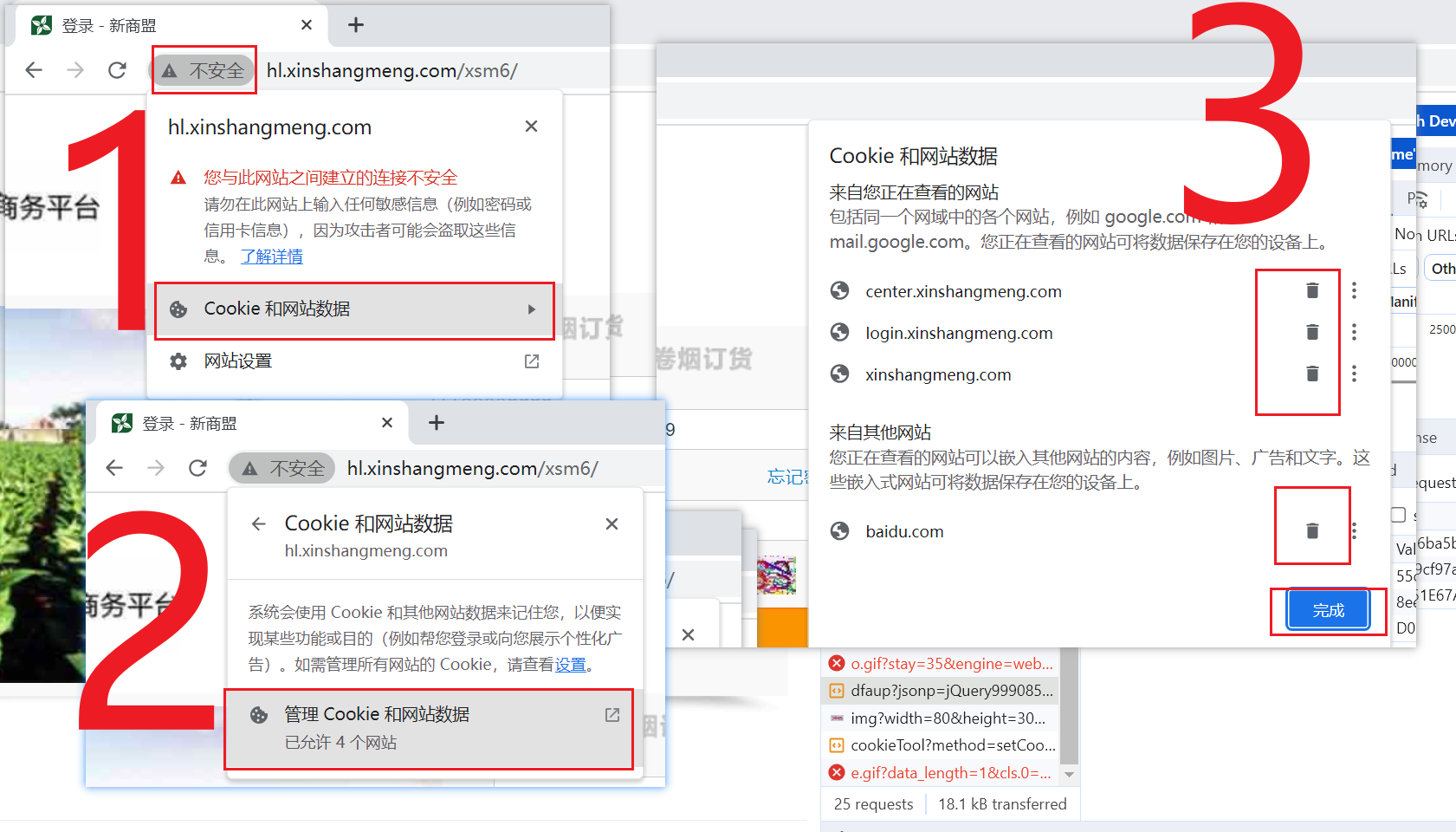
清楚过后可以看到已经不需要验证码了
我们依旧调试查看
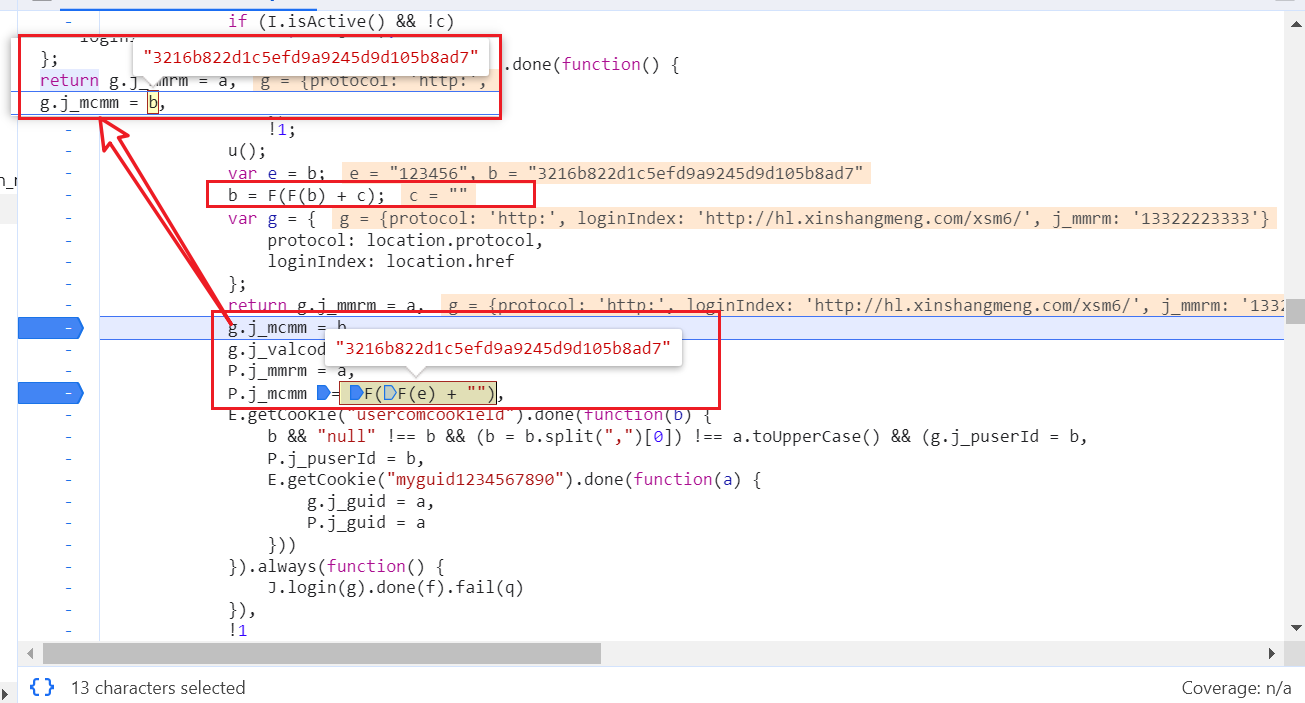
可以看到他就是F(F(b)+c)
b是你的密码
c是验证码
先把b用F函数加密一次
在把加密后的密码加上验证码在加密一次
就是返回的值
验证码是不缺定的数,所以我们只需要让他没有验证码就行
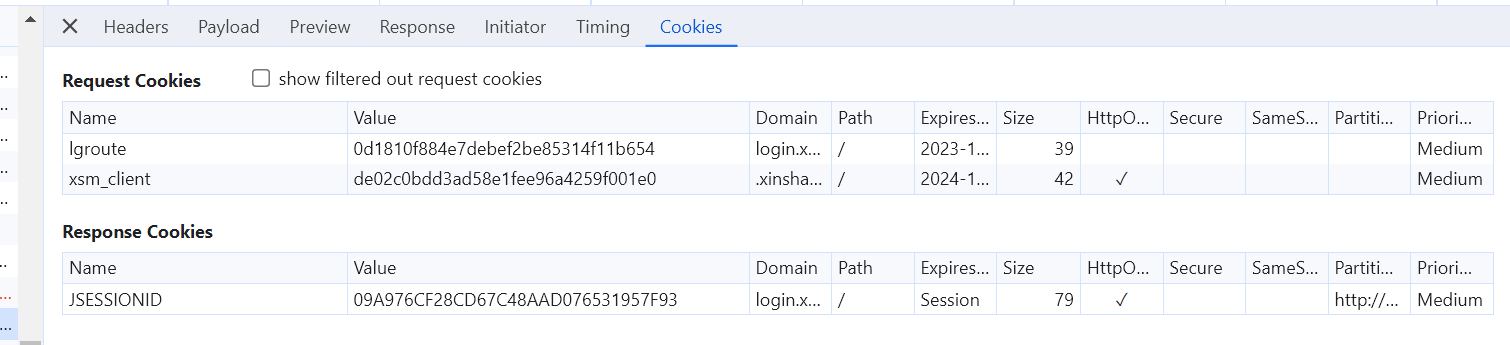
可以看到 没有验证码的cookies和有验证码的cookies不一样
所以我们这里使用selenium获取cookies,
这样的话,我们每次请求用的都是最新的cookies,就不会有验证码的问题
就彻底解决了验证码的问题
5 selenium获取cookies
使用selenium的无界面模式,并且掩盖selenium的自动化操作获取cookies
from selenium.webdriver.chrome.service import Service
from selenium import webdriver
# 获取最新的cookies,破解验证码
def get_cookies():
# 使用chrome开发者模式
options = webdriver.ChromeOptions()
options.add_experimental_option('excludeSwitches', ['enable-automation'])
# 禁用启用Blink运行时的功能
options.add_argument("--disable-blink-features=AutomationControlled")
# 无界面模式
options.add_argument('--headless')
# Selenium执行cdp命令 再次覆盖window.navigator.webdriver的值
# Chrome驱动
service = Service(executable_path=r"X:\Python_selenium驱动\chromedriver-win64\chromedriver.exe")
driver = webdriver.Chrome(options=options,service=service)
driver.execute_cdp_cmd("Page.addScriptToEvaluateOnNewDocument", {
"source": """
Object.defineProperty(navigator, 'webdriver', {
get: () => undefined
})
"""
})
url1 = 'http://hl.xinshangmeng.com/xsm6/'
# 获取cookie
driver.get(url1)
cookie = driver.get_cookies()
# print(cookie)
cookies = {cookie[i].get('name'):cookie[i].get('value') for i in range(len(cookie))}
# print(cookies)
return cookies
cookies = get_cookies()
print(cookies)
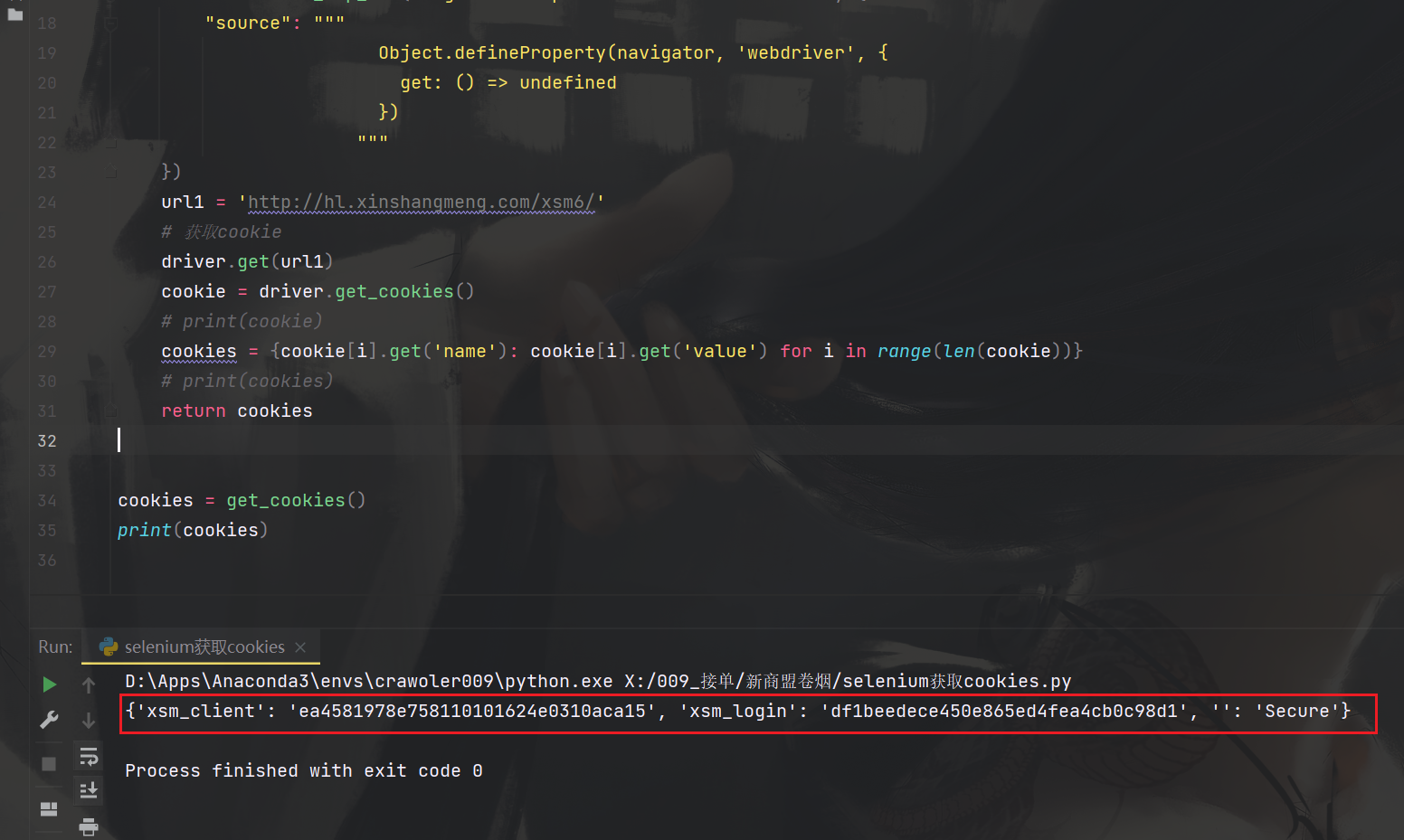
可以看到成功的获取了cookies,直接放入请求头中即可
6 完成代码展示
from selenium.webdriver.chrome.service import Service
from selenium import webdriver
import requests
import execjs
# 获取最新的cookies,破解验证码
def get_cookies():
# 使用chrome开发者模式
options = webdriver.ChromeOptions()
options.add_experimental_option('excludeSwitches', ['enable-automation'])
# 禁用启用Blink运行时的功能
options.add_argument("--disable-blink-features=AutomationControlled")
# 无界面模式
options.add_argument('--headless')
# Selenium执行cdp命令 再次覆盖window.navigator.webdriver的值
service = Service(executable_path=r"X:\Python_selenium驱动\chromedriver-win64\chromedriver.exe")
driver = webdriver.Chrome(options=options, service=service)
driver.execute_cdp_cmd("Page.addScriptToEvaluateOnNewDocument", {
"source": """
Object.defineProperty(navigator, 'webdriver', {
get: () => undefined
})
"""
})
url1 = 'http://hl.xinshangmeng.com/xsm6/'
# 获取cookie
driver.get(url1)
cookie = driver.get_cookies()
# print(cookie)
cookies = {cookie[i].get('name'): cookie[i].get('value') for i in range(len(cookie))}
# print(cookies)
return cookies
# 获取返回的数据
def get_data(username):
headers = {
"Referer": "http://hl.xinshangmeng.com/",
"User-Agent": "你的User-Agent"
}
# 获取最新的cookies,破解验证码
cookies = get_cookies()
print('cookies:',cookies)
url = "http://login.xinshangmeng.com/login/users/dologin/dfaup"
f = open('新商盟js.js','r',encoding='utf-8')
text = f.read()
f.close()
js = execjs.compile(text)
pwd = input('请输入密码:')
res = js.call('pwd',pwd) # call(func,*args) 第一个参数为函数,后面都为参数
print('j_mcmm:',res)
params = {
"j_mmrm": str(username),
"j_mcmm": res,
}
response = requests.get(url, headers=headers, cookies=cookies, params=params)
print(response)
print(response.text)
if __name__ == '__main__':
# 参数为账号
get_data(15666668888)
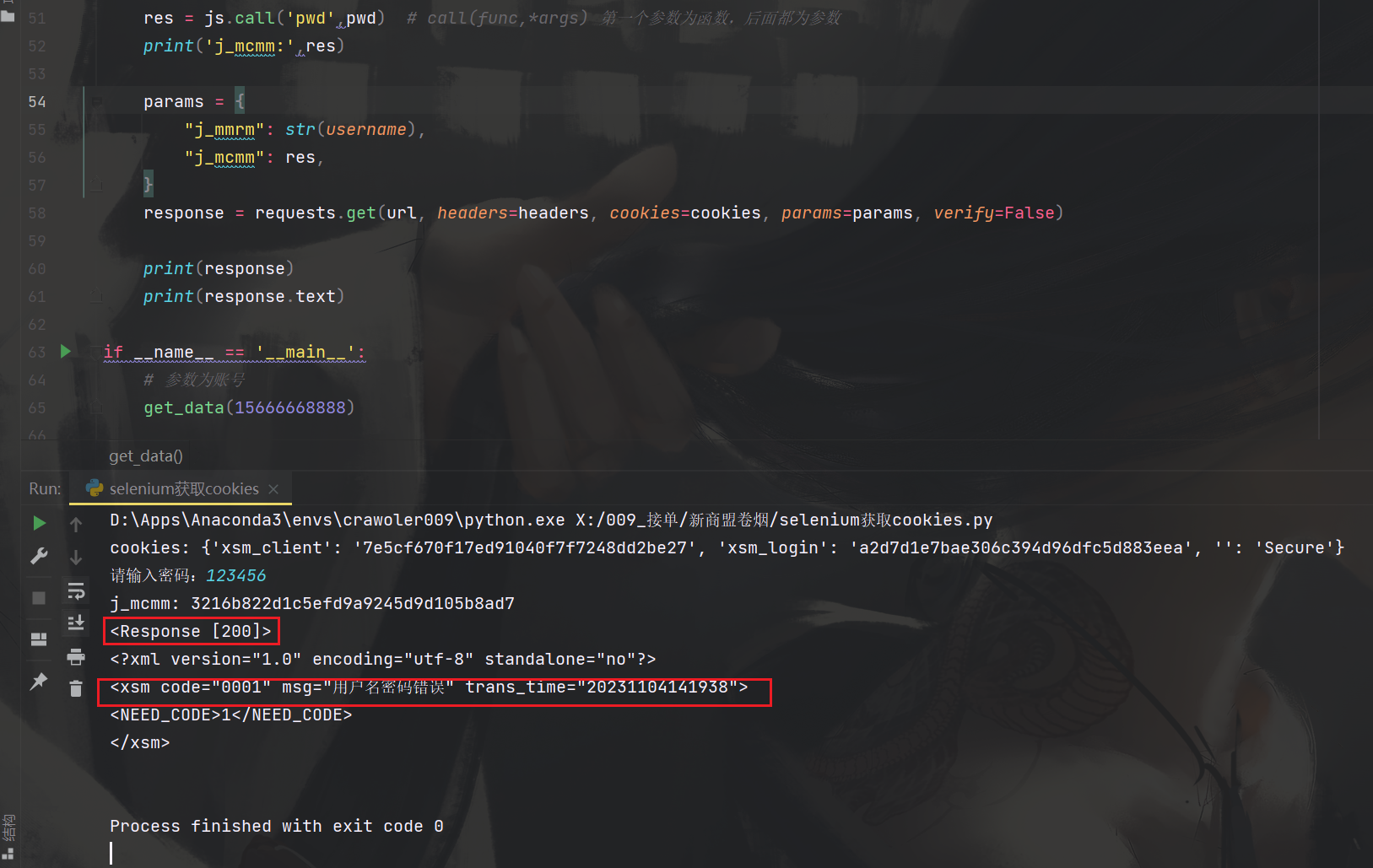
可以看到也是成功破解了,返回的不是验证码错误之类的
但是返回结果和网页上的不一样
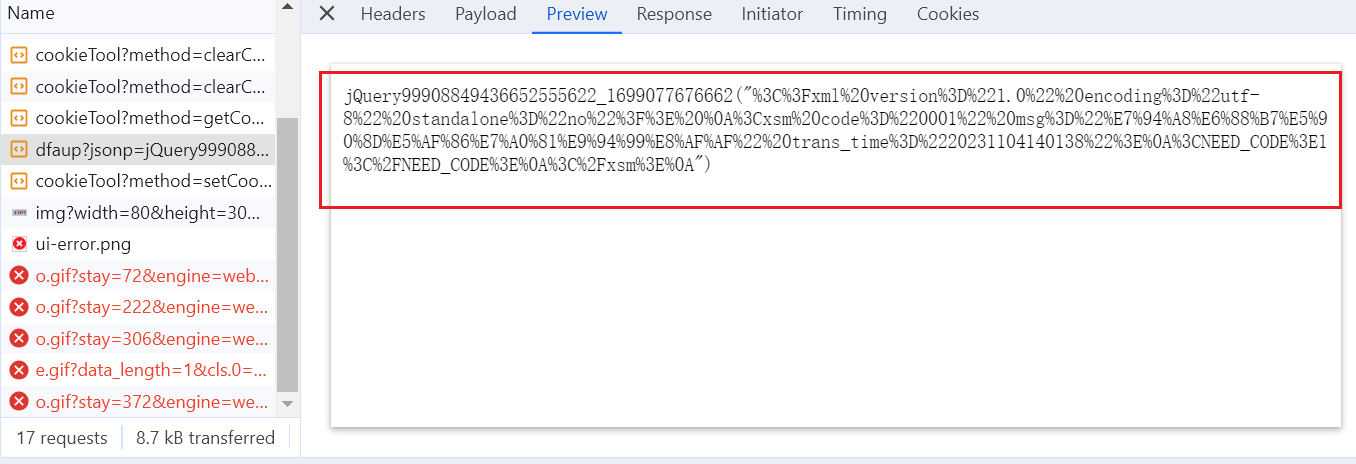
这是因为"jsonp"这个参数,他把数据转换为jquery对象
jsonp参数前面的值都是一样的,只不过下划线之后的值是一个时间戳

带上的话,就是和网页上一样了
有问题欢迎评论,如果对你有帮助可以点个赞
或者我哪里不对欢迎大家指出